With ordinary KVM switches, I believe, many have come across. The abbreviation "KVM" stands for "Keyboard Video Mouse". A KVM device allows, having only one set of keyboard + monitor + mouse (K.M.M.), to control several computers ( system blocks). In other words, we take N system blocks, connect their outputs from K.M.M. to the KVM device, and already to the device itself we connect a real monitor, keyboard and mouse. Switching between computers using KVM, we can see what is happening on the screen of the selected computer, as well as control it as if we were connected to it directly.
This is convenient if we need several machines for work, but access to them at the same time is not required. In addition, space is greatly saved - monitors, even liquid crystal ones, take up a fairly large amount of space on the table. Yes, and they don't cost much. And in a bunch of keyboards and mice on the table, you can quickly get confused ...
Advanced readers will object - why such difficulties if computers are most likely connected to one local network and you can use the built-in operating system (or external) programs remote access, such as Terminal Services or Radmin under Windows, VNC, ssh under *nix-like operating systems. Everything is correct, but what to do if, for example, you need to enter the computer's BIOS or the operating system has stopped loading because we installed some wrong driver or program? Or do we have several operating systems installed on the computer and we needed to choose the wrong one that starts by default? In general, all these programs are really good, but up to certain limits - as long as the computer's OS is operational and we only need access to the computer after this OS boots up.
For example, let's look at a few typical KVM switches using the example of devices manufactured by the company.
Device Specifications
CN-6000 supports the separation of powers between users and allows you to create up to 64 administrative or user accounts, of which up to 16 accounts can work with the device at the same time. The device has a built-in WEB-interface for administration, and its small size allows it to be placed on a table or mounted (using a special bracket included in the kit) on a side truss of a rack (0U rack mountable). CN-6000 supports firmware upgrade via Ethernet connection (web interface or native utility). The maximum video resolution supported by the device is 1600x1200 pixels.
Summary table of specifications:
| Hardware requirement (remote client) | Pentium III 1Ghz | ||
| Interfaces | local console | Keyboard | 1 × Mini-DIN-6 F(Purple) |
| Video | 1 × HDB-15 F(Blue) | ||
| Mouse | 1 × HDB-15 F(green) | ||
| System (KVM) | 1 × SPHD-15F(Yellow) | ||
| LAN port | 1 x RJ-45(F) | ||
| Power on the net (reserved) | 1 × DB9(M) | ||
| Power interface | 1 | ||
| Buttons/switches | KVM Reset | 1 × semi-concealed, front | |
| Indicators | food | 1 × orange | |
| remote user connection | 1 x green | ||
| LAN 10/100 Mbps | 1 × green/orange | ||
| Supported protocols | 10baseT Ethernet and 100baseTX Fast Ethernet. TCP/IP | ||
| Video permissions | Up to 1600×1200 60Hz | ||
| Frame | metal | ||
| Dimensions (length × width × height) | 200×80×25mm | ||
Let's move on to the tests.
There are four utilities on the CD that comes with the kit:
- CN6000 Client is a Windows client program that allows you to connect to a remote computer
- a similar client program written in Java (in jar format)
- CN6000 Admin Tool - device configuration manager (under Windows)
- log server - a program that can be configured to receive and store log files from the CN-6000
In addition, a WEB server is built into the KVM switch, so the device can be accessed through a WEB browser. But we will return to the web interface a little later, first we will consider individual utilities.
Configuring the CN-6000 through the Admin Tool.
The program is designed to configure the device, set access passwords, security, etc.
When it was launched, it was not without curiosity:

The first time you run all the utilities from the included disc, you are required to enter a serial number. In the documentation (even latest version, which lies on the manufacturer's website) it is said that the serial number is printed on the bottom of the CN-6000 case. And some kind of serial number is indeed printed there, only it is much shorter than the programs require. In general, having suffered a little, entering the serial number found this way and that, adding zeros or spaces to it and not reaching anything more than the "Invalid Serial Number" window, I already wanted to finish testing the device that day. Taking the CD out of the CD-ROM (I inserted it into the CD-drive in the first place - I had to install the software), I found a strange sticker on the disk - this turned out to be the coveted serial number.
Of course, theoretically, a person can pay attention to what is written or pasted on the CD when he inserts it into the drive. But how many immediately pay attention to this? :) And, one wonders, why was it necessary to write deliberately false information in the documentation? I repeat - the site contains more a new version Documentation and there this "typo" is not corrected. I note that this is not the last inaccuracy that slips through the documentation, so sometimes you have to act according to the saying "do not believe your eyes."

The CN-6000 administration utility is useful in that it allows you to find a device on the network, even if its IP address does not belong to the subnet we are in, just enough that we (the computer from which we are trying to access the CN-6000 ) were on the same LAN segment as the KVM switch.
After entering the username and password, we get to the device configuration menu:

ATEN has taken a good approach to the issue of device security. When you first enter the device configuration, we are warned that it would be nice to change the standard login and password ...

In section network IP addressing of the device is configured, ports for remote access to computers controlled by CN-6000 are set. And also here you can specify the MAC address of the machine on which the "Log Server" program is located, which stores the log files (events) sent from the KVM switch (if it is not set, the logs will be stored on the KVM itself and you can see them from the web interface). This machine (for the Log-server) can be any computer on which Windows is installed and the program under discussion is running. The only problem is that the computer must be in the same network segment (roughly speaking, connected to the same switch) as the KVM CN-6000 itself, so the usefulness of this "feature" is questionable.

Bookmarked security filters (by MAC and/or IP addresses) for access to the remote screen of administered computers are configured, as well as a filter for administration of the CN-6000 itself.

In the next tab, user names and passwords are set, as well as their rights. Remarkably, you can restrict logins for configuring the CN-6000 and using the JAVA client. The minimum password length that the configuration utility accepts is eight characters. It is a pity, of course, that the password is not checked for "simplicity", but even checking the length of the password indicates that ATEN pays attention to security.

The last tab allows you to update the firmware of the device, enable the possibility of simultaneous connection to a remote computer for several people (although the mouse and keyboard are still the same, from the point of view of the controlled computer, so one controls, the rest look ... or interfere with each other by dragging the mouse to different sides). The reaction to an incorrect authentication process is immediately configured, as well as the inclusion of various "hidden" modes of the CN-6000 (no response to ping and a ban on showing itself when automatic search devices on the local network via the client utility or administration utility).
In the same tab there is another item - Reset on Exit. I would assume that this is a reset to default settings, but in this case this implies rebooting the device when exiting the configuration utility. Otherwise (if it is not rebooted), the new settings, although they will be remembered, will not be applied (until the reboot).
At this point, consideration of the configuration utility can be considered complete (another aspect will be discussed in the section on the Java client).
Let's go to the web interface.
Configuration via WEB-interface

In order to get into the web interface of the device, it is enough to type the IP address that is set on the CN-6000 in any browser.
It is noteworthy that the browser immediately redirects the client to a connection via HTTPS://, i.e. all further work takes place through a secure SSL connection.

After entering the login and password, the icons on the left and at the top of the web interface become active (you can click on them).

The top icons open sections related to configuring the CN-6000. For the most part, all the options there repeat the options of the Windows utility interface. AdminTool, but there are some differences. For example, in this window (configuring network addresses), we can only set the IP address of the device, but we cannot specify the subnet mask and gateway. In addition, setting the IP address works somehow crookedly - I was not able to change the device's IP address from the web interface (using the Admin Tools utility, it changed without problems).

Here is what you can see in the Admin Tool utility when you try to change the address through the web interface from 10.0.0.9 to 192.168.0.1. For some reason, the subnet mask changed from the standard 255.255.255.0 to 10.0.0.9, and the device (after a reboot) replies at 192.168.0.1 for 5 seconds, and then starts responding at 10.0.0.9 (it completely forgets about 192.168.0.1). This may be a bug in the current firmware version (1.5.141), but this version, at the time of testing, was the latest one that could be found on the company's website.
No more bugs related to the web interface were found during testing.

Chapter security repeats the same section in the Admin Tool.

A similar situation with the section User Manager…

... and section customization.

Icon Log, located on the left side of the web interface, allows you to view the events that occurred during the operation of the device. In this case, the screenshot reflects the logs that appeared at the time the device was tested by Nessus.
As mentioned above, logs can be dumped to an external log server (but with certain restrictions on its location).
Today, many tasks that were traditionally assigned to several physical servers are being transferred to virtual environments. Virtualization technologies are also in demand by software developers, since they allow comprehensive testing of applications in various operating systems. At the same time, simplifying many issues, virtualization systems themselves need to be managed, and one cannot do without special solutions.
Vagrant
The VirtualBox virtual machine is deservedly popular among administrators and developers, allowing you to quickly create the necessary environments using a graphical interface or command line interface. If the number of VMs does not exceed three, there are no difficulties in deployment and management, but modern projects tend to acquire configurations, and as a result, a very complex infrastructure is obtained, which becomes difficult to handle. This is the problem that the Vagrant virtual environment manager is designed to solve, allowing you to create copies of virtual machines with a predefined configuration and dynamically reallocate VM resources (Provisioning) as needed. In the basic distribution, Vagrant works with VirtualBox, but the plugin system allows you to connect another virtualization system. Today, the plugin code for AWS and Rackspace Cloud is open, and a plugin is available for commercial subscription to support VMware Fusion/Workstation.
Vagrant does not create a virtual machine from scratch. For convenience, the project offers several base images (boxes), which are imported and subsequently used for quick deployment of the system, already on the basis of boxes, a guest OS is assembled with the desired configuration.
Chef and Puppet are pre-installed in boxes to simplify application deployment. In addition, the desired settings can be specified using the shell. The environments include a complete set for running and developing applications in Ruby. SSH is used to access the VM, it is possible to exchange files through a shared directory.
Written by Vagrant using Ruby, it can be installed on any platform for which there are VirtualBox and Ruby components. Packages for Windows, Linux (deb and rpm) and OS X are available on the download page.
The process of installing and using Ubuntu is simple. Download the VirtualBox and Vagrant packages and install:
$ sudo dpkg -i virtualbox-4.2.10_amd64.deb $ sudo dpkg -i vagrant_1.2.2_x86_64.deb
At the time of this writing, with the latest up-to-date version of VirtualBox 4.2.14, there were problems when starting Vagrant, so for now it is better to use 4.2.12 or test 4.2.15. Alternatively, you can do:
$ cd ~/.vagrant.d/boxes/BoxName/virtualbox $ openssl sha1 *.vmdk *.ovf > box.mf
Here is an alternative way to install Vagrant - using Ruby:
$ sudo apt-get install ruby1.8 ruby1.8-dev rubygems1.8 $ sudo gem install vagrant
All project settings are made in a special Vagrantfile . In order not to create a template manually, it can be generated as follows:
$ mkdir project $ cd project $ vagrant init
Now you can look into the created configuration file and fill in: VM settings (config.vm. ), SSH connection options (config.ssh.), the parameters of Vagrant itself (config.vagrant). All of them are well documented, the meaning of some is clear and without explanation.
In fact, several such files are used at startup, each subsequent one overrides the previous one: built into Vagrant (it cannot be changed), supplied with boxes (packed using the "--vagrantfile" switch), located in ~/.vagrant.d and the project file . This approach allows you to use the default settings, overriding only what is necessary in a particular project.

All installations are done using the vagrant command, the list of available keys can be viewed using "-h". After installation, we do not have a single image, running vagrant box list will display an empty list. The finished box can be located in a local file system or on a remote server, its name is set as a parameter, which will be used in projects. For example, we use the official Box Ubuntu 12.04 LTS offered by Vagrant developers.
$ vagrant box add precise64 http://files.vagrantup.com/precise64.box
Now it can be accessed from Vagrantfile:
config.vm.box = "precise64"
Although it’s easier to specify it right away when initializing the project:
$ vagrant init precise64
The easiest way, which does not require learning Chef and Puppet, is to use standard shell commands to configure the VM, which can be written directly in the Vagrantfile or, even better, combined into a script that is connected like this:
Vagrant.configure("2") do |config| config.vm.provision:shell, :inline => "script.sh" end
Now all the commands specified in script.sh will be executed when the VM starts up. When the project is started, an ovf file is created, its settings can be viewed using the VirtualBox GUI or the VBoxManage command:
$ VBoxManage import /home/user/.vagrant.d/boxes/precise64/virtualbox/box.ovf Virtual system 0: 0: Suggested OS type: "Ubuntu_64" (change with "--vsys 0 --ostype
They do not always satisfy the specified conditions, but using the provider settings, you can easily change the settings of a particular VM (see the “change with ...” tips):
Config.vm.provider:virtualbox do |vb| vb.customize ["modifyvm", :id, "--memory", "1024"] end
Launch and connect to the system via SSH:
$ vagrant up $ vagrant ssh
To stop the VM, use the halt or destroy parameter (the second one will clear all files, the next time all operations will be performed from the beginning), if you need to send it to hibernation - vagrant suspend , return - vagrant resume . For an example of working with Chef, you can use a ready-made recipe with which to configure APT and Apache2:
Config.vm.provision:chef_solo do |chef| chef.recipe_url = "http://files.vagrantup.com/getting_started/cookbooks.tar.gz" chef.add_recipe("vagrant_main") end
To access the VM "from the outside", you will need to configure port forwarding. By default, forwarding 22 -> 2222 is performed, allowing you to connect via SSH. Add to Vagrantfile:
Vagrant::Config.run do |config| config.vm.forward_port 80, 1111 end
The web server can now be accessed by navigating to http://127.0.0.1:1111/. In order not to configure the environment every time, it is better to build a ready-made package based on it.
$ vagrant package --vagrantfile Vagrantfile --output project.box
Now the project.box file can be distributed to other administrators, developers, or ordinary users who will include it using the vagrant box add project.box command.
Convirt
Xen/KVM virtualization systems released under free licenses do not have a user-friendly interface, which is often interpreted not in their favor. However, this shortcoming is easily remedied. ConVirt allows you to deploy virtual machines across multiple Xen and KVM servers with just one click, using an easy-to-use interface. All necessary operations with virtual machines are available: start, stop, create snapshots, control and redistribute resources, connect to a VM via VNC, automate administration tasks. Ajax technology makes the interface interactive and similar to a desktop application. For example, a VM can be simply dragged from one server to another. The interface is not localized, but the controls are intuitive.

Server pooling allows you to configure and control virtual machines and resources at the server pool level, rather than separate server. Agents are not installed on virtual systems, only the convirt-tool package on the physical server is needed. This simplifies administration and deployment.
Once a new server is added, ConVirt will automatically collect its configuration and performance data, providing summary information at several levels - from a single virtual machine, a physical server, to the entire pool. The collected data is used to automatically host new guest systems. This information is also displayed in the form of visual graphs.
To create virtual machines, templates are used - descriptions of the virtual machine settings, containing data on the resources allocated, the path to the OS files and additional settings. After installation, several ready-made templates are available, but if necessary, it is easy to create them yourself.
All technologies are supported: load balancing, hot migration, virtual disks with growing capacity, allowing you to use resources as needed, and many other features implemented in Xen and KVM. You don't need to stop the VM to reallocate resources.
Implemented the ability to manage a virtual environment for several administrators with the ability to audit and control their actions.
ConVirt is developed by the Convirture company, using the open core concept (open basis), when only a basic set of functions is freely distributed with the source texts, the rest is available in the commercial version. The open source version lacks High Availability support, VLAN integration, redundancy and recovery, command line management, notifications, and official support.
During development, the TurboGears2 framework, ExtJs and FLOT libraries were used, MySQL was used for storing information, dnsmasq was used as a DHCP and DNS server. The required package can be found in the repositories of popular Linux distributions.
Karesansui
All possibilities for managing virtual environments are implemented: OS installation, creation of disk subsystem and virtual environment configurations. network cards, quota management, replication, freeze VM, create snapshots, view detailed statistics and log data, load monitoring. From one console, you can manage multiple physical servers and the virtual machines hosted on them. Multi-user work with separation of rights is possible. As a result, the developers managed to implement a virtual environment in the browser that allows you to fully manage the systems.
Written by Karesansui in Python, SQLite is used as a DBMS for a single-node system. If you plan to manage Karesansui installations hosted on multiple physical servers, MySQL or PostgreSQL should be used.
You can deploy Karesansui on any Linux. The developers themselves prefer CentOS (for which the site has detailed instructions), although Karesansui does well on Debian and Ubuntu. Before installation, you must fulfill all the dependencies indicated in the documentation. Next, the installation script is launched and the database is initialized. If a multi-server configuration is used, then you just need to specify an external database.
Subsequent work fully compensates for the inconvenience of installation. All settings are divided into seven tabs, the purpose of which is clear from the name: Guest, Settings, Job, Network, Storage, Report and Log. Depending on the user's role, not all of them will be available to him.
You can create a new VM from a local ISO file or by specifying an HTTP/FTP resource with installation images. You will also need to set other attributes: the system name that will be displayed in the list, network name (hostname), virtualization technology (Xen or KVM), RAM size, and hard drive(Memory Size and Disk Size) - and choose a picture that will match the virtual OS, making it easier to quickly visually select it in the console.
WebVirtMgr
The capabilities of the described solutions are often redundant, and their installation is not always clear to an administrator with little experience. But there is a way out here too. The WebVirtMgr virtual machine centralized management service was created as a simple replacement for virt-manager, which will provide comfortable work with a VM using a browser with a Java plugin installed. KVM settings management is supported: creation, installation, configuration, launch of VM, snapshots and backup of virtual machines. Provides management of the network pool and storage pool, working with ISO, cloning images, viewing CPU and RAM usage. The virtual machine is accessed via VNC. All transactions are recorded in logs. With a single installation of WebVirtMgr, you can manage multiple KVM servers. RPC libvirt (TCP/16509) or SSH is used to connect to them.

The interface is written in Python/Django. You will need a Linux server to install. Distributed in source and RPM packages for CentOS, RHEL, Fedora and Oracle Linux 6. The deployment process itself is simple and well described in the project documentation (in Russian), you just need to configure libvirt and install webvirtmgr. The whole process takes five minutes. After connecting to the Dashboard, select Add Connection and specify the node parameters, then we can configure the VM.
Scripting the creation of a VM
The simplest script for creating and running a virtual machine using VirtualBox:
#!/bin/bash vmname="debian01" VBoxManage createvm --name $(vmname) --ostype "Debian" --register VBoxManage modifyvm $(vmname) --memory 512 --acpi on --boot1 dvd VBoxManage createhd - -filename "$(vmname).vdi" --size 10000 --variant Fixed VBoxManage storagectl $(vmname) --name "IDE Controller" --add ide --controller PIIX4 VBoxManage storageattach $(vmname) --storagectl "IDE Controller" --port 0 --device 0 --type hdd --medium "$(vmname).vdi" VBoxManage storageattach $(vmname) --storagectl "IDE Controller" --port 0 --device 1 --type dvddrive --medium /iso/debian-7.1.0-i386-netinst.iso VBoxManage modifyvm $(vmname) --nic1 bridged --bridgeadapter1 eth0 --cableconnected1 on VBoxManage modifyvm $(vmname) --vrde on screen VBoxHeadless --startvm $(vmname)
Proxmox VE
The previous solutions are good for those situations where there is already some infrastructure. But if you only have to deploy it, you should think about specialized platforms that allow you to quickly get the desired result. An example here is Proxmox Virtual Environment , which is a Linux distribution (based on Debian 7.0 Wheezy) that allows you to quickly build a virtual server infrastructure using OpenVZ and KVM and is practically on par with products such as VMware vSphere, MS Hyper-V and Citrix XenServer .

In fact, the system should only be installed (a couple of simple steps), everything else already works out of the box. Then, using the web interface, you can create a VM. For this purpose, the easiest way is to use OpenVZ templates and containers, which are loaded from external resources directly from the interface with one click (if manually, then copy to the /var/lib/vz/template directory). But templates can also be created by cloning already created systems in the linking mode. This option saves disk space because all linked environments use only one shared copy of the reference template data without duplicating information. The interface is localized and understandable, you do not experience any particular inconvenience when working with it.
There is support for clusters, tools for Reserve copy virtual environments, it is possible to migrate VM between nodes without stopping work. Access control to existing objects (VM, storage, nodes) is implemented on the basis of roles, various authentication mechanisms are supported (AD, LDAP, Linux PAM, built-in Proxmox VE). The web interface provides the ability to access the VM using VNC and SSH consoles, you can view the status of jobs, logs, monitoring data and much more. True, some operations specific to HA systems will still have to be performed the old fashioned way in the console, such as creating an authorized iSCSI connection, configuring a cluster, creating multipath, and some other operations.
System requirements are low: x64 CPU (preferably with Intel VT/AMD-V), 1+ GB RAM. The project offers a ready-made ISO image and repository for Debian.
Conclusion
All the solutions described are good in their own way and do an excellent job with the tasks. You just need to choose the most suitable for a particular situation.
On Ubuntu, it is recommended to use the KVM hypervisor (virtual machine manager) and the libvirt library as a tool to manage it. Libvirt includes a set of software APIs and custom virtual machine (VM) management applications virt-manager (graphical interface, GUI) or virsh ( command line, CLI). As alternative managers, you can use convirt (GUI) or convirt2 (WEB interface).
Currently, only the KVM hypervisor is officially supported in Ubuntu. This hypervisor is part of the kernel code operating system linux. Unlike Xen, KVM does not support paravirtualization, which means that in order to use it, your CPU must support VT technologies. You can check if your processor supports this technology by running the command in the terminal:
If the result is a message:
INFO: /dev/kvm exists KVM acceleration can be used
so KVM will work without problems.
If the output is a message:
Your CPU does not support KVM extensions KVM acceleration can NOT be used
then you can still use the virtual machine, but it will be much slower.
Install as guest 64-bit systems
Allocate more than 2 GB of RAM to guests
Installation
sudo apt-get install qemu-kvm libvirt-bin ubuntu-vm-builder bridge-utils
This is an installation on a server without X, i.e. does not include a graphical interface. You can install it with the command
sudo apt-get install virt-manager
After that, the “Virtual Machine Manager” item will appear in the menu and, with a high degree of probability, everything will work. If any problems still arise, then you will need to read the instructions in the English-language wiki.
Create a guest system
The procedure for creating a guest system using the graphical interface is quite simple.
But the text mode can be described.
qcow2
When creating a system using the graphical interface, you are prompted to either select an existing image file or block device as a hard disk, or create a new file with raw (RAW) data. However, this is far from the only available file format. Of all the disk types listed in man qemu-img, qcow2 is the most flexible and up-to-date. It supports snapshots, encryption and compression. It must be created before creating a new guest system.
Qemu-img create -o preallocation=metadata -f qcow2 qcow2.img 20G
According to the same man qemu-img , metadata preallocation (-o preallocation=metadata) makes the disk slightly larger initially, but provides better performance when the image needs to grow. In fact, in this case, this option avoids an unpleasant bug. The created image initially takes up less than a megabyte of space and grows to the specified size as needed. The guest system should immediately see this final specified size, however, during the installation phase, it can see the actual size of the file. Naturally, it will refuse to be installed on a 200 kb hard drive. The bug is not specific to Ubuntu, it also appears in RHEL, at least.
In addition to the type of image, you can later choose how to connect it - IDE, SCSI or Virtio Disk. The performance of the disk subsystem will depend on this choice. There is no unambiguously correct answer, you need to choose based on the task that will be assigned to the guest system. If the guest system is created "to see", then any method will do. In general, it is usually I / O that is the bottleneck of a virtual machine, therefore, when creating a highly loaded system, this issue should be taken as responsibly as possible.
Kimchi is a HTML5 based web interface for KVM. It provides an easy and flexible interface to create and manage a guest virtual machine. Kimchi is installed and runs as a daemon on the KVM host. It manages KVM guests with the help of libvirt. Kimchi interface supports all latest version of the browsers with -1 version, it also supports mobile browsers.
Kimchi can be installed on latest version of RHEL, Fedora, openSUSE and Ubuntu. In this guide, i used Ubuntu 14.10 as a KVM host.
Before configuring kimchi, you must install the following dependent packages.
$ sudo apt-get install gcc make autoconf automake gettext git python-cherrypy3 python-cheetah python-libvirt libvirt-bin python-imaging python-pam python-m2crypto python-jsonschema qemu-kvm libtool python-psutil python-ethtool sosreport python-ipaddr python-ldap python-lxml nfs-common open-iscsi lvm2 xsltproc python-parted nginx firewalld python-guestfs libguestfs-tools python-requests websockify novnc spice-html5 wget
System would ask you the following details during the installation of packages.
1. OK on Postfix configuration.
2. Select Internet Site on general type of mail configuration.
3. Type your FQDN and then select OK.
Once installed, download the latest version of kimchi from github.
$ wget https://github.com/kimchi-project/kimchi/archive/master.zip
Unzip the downloaded file.
$ unzip master.zip $ cd kimchi-master/
Build kimchi using the following command.
$ ./autogen.sh --system
$ make $ sudo make install # Optional if running from the source tree
$ sudo kimchid --host=0.0.0.0
Access kimchi using web browser, https://localhost:8001. You would be asked to login, use your system credential which you normally use for login to system.

Once you logged in, you will get a page like below. This show the list of running guest virtual machines on current host, you have buttons to perform shutdown, restart and connect to console by clicking on action.
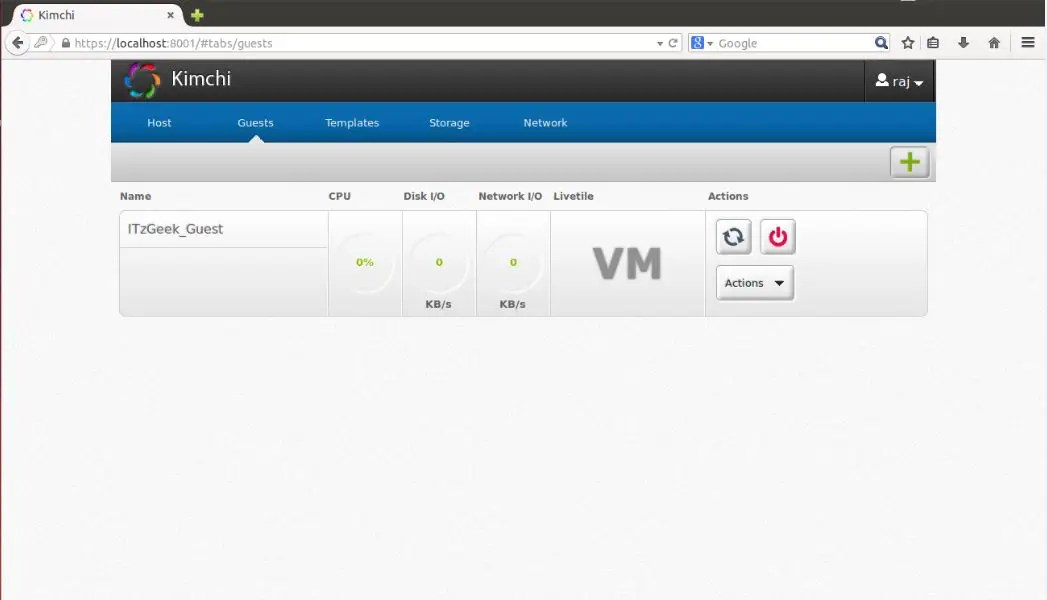
To create a new guest machine, click on the + sign in the right corner. If you use this option to create a machine, it will be done through templates.

You can manage templates by visiting templates menu. To create a new template, click on the + sign in the right corner. You can create a template using ISO images, you can place iso images on /var/lib/kimchi/isos or use remote one.

You can manage storage pool by going to storage menu, there you can add a new storage by clicking on + sign. It supports adding NFS, iSCSI and SCSI fiber channel storage.

Network can be managed by going to network menu, you can create a new network with isolated, NAT and bridged networking.

KVM or Kernel Virtual Module is a virtualization module for the Linux kernel that allows you to turn your computer into a hypervisor to manage virtual machines. This module operates at the kernel level and supports hardware acceleration technologies such as Intel VT and AMD SVM.
By itself software KVM in user space does not virtualize anything. Instead, it uses the /dev/kvm file to set up virtual address spaces for the guest machine in the kernel. Each guest machine will have its own video card, network and sound card, HDD and other equipment.
Also, the guest system will not have access to the components of the real operating system. The virtual machine runs in a completely isolated space. You can use kvm both on a GUI system and on servers. In this article, we'll walk you through installing kvm Ubuntu 16.04.
Before proceeding to the KVM installation itself, you need to check whether your processor supports hardware virtualization acceleration from Intel-VT or AMD-V. To do this, run the following command:
egrep -c "(vmx|svm)" /proc/cpuinfo
If the result is 0, then your processor does not support hardware virtualization, if 1 or more, then you can use KVM on your machine.
Now we can move on to installing KVM, a set of programs can be obtained directly from the official repositories:
sudo apt install qemu-kvm libvirt-bin bridge-utils virt-manager cpu-checker
We installed not only the kvm utility, but also the libvirt library, as well as the virtual machine manager. After the installation is complete, you need to add your user to the libvirtd group, because only root and users of this group can use KVM virtual machines:
sudo gpasswd -a USER libvirtd
After executing this command, log out and log in again. Next, let's check if everything was installed correctly. To do this, use the kvm-ok command:
INFO: /dev/kvm exists
KVM acceleration can be used
If everything was done correctly, then you will see the same message.
Using KVM on Ubuntu 16.04
You have completed the task of installing kvm on Ubuntu, but you cannot use this virtualization environment yet, but it still needs to be configured. Next, we'll look at how Ubuntu's kvm setup is done. First you need to set up the network. We need to create a bridge with which the virtual machine will connect to the computer's network.
Bridge configuration in NetworkManager
This can be done in several ways, for example, you can use the NetworkManager network configuration program.
Click the NetworkManager icon in the panel, then select change connections, then click the button Add:

Then select connection type Bridge and press Create:

In the window that opens, click the button Add, to link our bridge to the internet connection:

Select from the list ethernet and press Create:

In the next window, select in the field device, network interface, with which our bridge should be connected:

Now you will see your bridge in the list of network connections. It remains to restart the network in order to fully apply the changes, to do this, run:
Manual bridge setting
First you need to install the bridge-utils set of utilities if you haven't already:
sudo apt install bridge-utils
Then, using the brctl program, we can create the bridge we need. To do this, use the following commands:
sudo brctl addbr bridge0
$ sudo ip addr show
$ sudo addif bridge0 eth0
The first command adds the br0 bridge device, with the second you need to determine which network interface is the main connection to the external network, in my case it is eth0. And with the last command, we bind bridge br0 to eth0.
Now you need to add a few lines to the network settings so that everything rises automatically after the system starts. To do this, open the /etc/network/interfaces file and add the following lines there:
sudo gedit /etc/network/interfaces
loopback
auto lo bridge0
iface lo inet loopback
iface bridge0 inet dhcp
bridge_ports eth0
When the settings are added, restart the network:
sudo systemctl restart networking
Now the installation and configuration of KVM is complete and you can create your first virtual machine. After that, you can view the available bridges with the command:

Creating KVM virtual machines
The Ubuntu KVM setup is complete and now we can move on to using it. First, let's look at the list of already existing virtual machines:
virsh -c qemu:///system list

It's empty. You can create a virtual machine through the terminal or in the graphical interface. To build from the terminal, use the virt-install command. First, let's go to the libvirt folder:
cd /var/lib/libvirt/boot/
To install CentOS, the command will look like this:
sudo virt-install \
--virt-type=kvm \
--name centos7\
--ram 2048\
--vcpus=2 \
--os-variant=rhel7 \
--hvm\
--cdrom=/var/lib/libvirt/boot/CentOS-7-x86_64-DVD-1511.iso \
--network=bridge=br0,model=virtio \
--graphics vnc\
--disk path=/var/lib/libvirt/images/centos7.qcow2,size=40,bus=virtio,format=qcow2
Let's take a closer look at what the parameters of this command mean:
- virt-type- type of virtualization, in our case kvm;
- name- name new car;
- ram- amount of memory in megabytes;
- vcpus- number of processor cores;
- os-variant- type of operating system;
- cdrom- installation image of the system;
- network-bridge - network bridge, which we set up earlier;
- graphics- how to get access to the graphical interface;
- diskpath- address of the new hard disk for this virtual machine;
After the installation of the virtual machine is completed, you can find out the connection settings via VNC using the command:
sudo virsh vncdisplay centos7
Now you can enter the received data in your VNC client and connect to the virtual machine even remotely. For Debian, the command will be slightly different, but everything looks similar:
Go to the folder for images:
cd /var/lib/libvirt/boot/
You can download the installation image from the Internet if necessary:
sudo wget https://mirrors.kernel.org/debian-cd/current/amd64/iso-dvd/debian-8.5.0-amd64-DVD-1.iso
Then let's create a virtual machine:
sudo virt-install \
--virt-type=kvm \
--name=debina8 \
--ram=2048 \
--vcpus=2 \
--os-variant=debian8 \
--hvm\
--cdrom=/var/lib/libvirt/boot/debian-8.5.0-amd64-DVD-1.iso \
--network=bridge=bridge0,model=virtio \
--graphics vnc\
--disk path=/var/lib/libvirt/images/debian8.qcow2,size=40,bus=virtio,format=qcow2
Now let's see the list of available machines again:
virsh -c qemu:///system list
To start the virtual machine, you can use the command:
sudo virsh start hostname
To stop:
sudo virsh shutdown hostname
To put into sleep mode:
sudo virsh suspend hostname
To reboot:
sudo virsh reboot hostname
sudo virsh reset hostname
To completely remove a virtual machine:
sudo virsh destroy hostname
Creating Virtual Machines in the GUI\
If you have access to a graphical interface then there is no need to use a terminal, you can use the full graphical interface of the Virtual Manager virtual machine manager. The program can be launched from the main menu:

To create a new machine, click on the icon with the monitor icon. Next, you will need to select an ISO image of your system. You can also use a real CD/DVD drive:

On the next screen, select the amount of memory that will be available for the virtual machine, as well as the number of processor cores:

On this screen, you need to select the hard drive size that will be available in your machine:

At the last step of the wizard, you have to check the correctness of the machine settings, as well as enter its name. You also need to specify the network bridge through which the machine will connect to the network:

After that, the machine will be ready for use and will appear in the list. You can launch it using the green triangle on the manager toolbar.
conclusions
In this article, we looked at how the Ubuntu 16.04 KVM installation is done, how to fully prepare this environment for work, as well as how to create virtual machines and use them. If you have any questions, ask in the comments!
At the end, a lecture from Yandex about what virtualization is in Linux:
 uptostart.ru News. Games. Instructions. Internet. Office.
uptostart.ru News. Games. Instructions. Internet. Office.